EPB allows you to extract an authentication token to iCloud Panel from a non-live Windows OS, e.g., by mounting the disk image of the operating system in which the token is stored.
To extract the authentication token to iCloud panel, do the following:
1.Mount the image of the disk containing the authentication token.
2.Run Elcomsoft Phone Breaker.
3.In the Tools menu, select the Apple tab.
4.Click Extract authentication token.
5.Define the path and password to the file containing the authentication token:
▪Path to MME token: Enter the path to com.apple.AOSKit.plist file. It is usually located in: %appdata%\Apple Computer\Preferences\ on Windows OS.
▪Password: Enter the password of the Windows user whose token you are extracting.
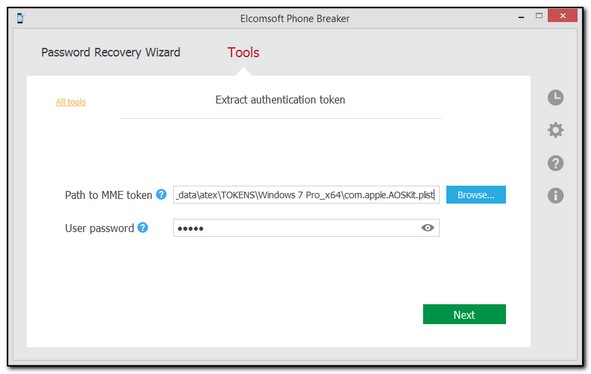
6. Click Next.
7. On the following page, define the path to user master key file and its SID. The user master key itself is displayed on top. This key is used to decrypt the authentication token.
•Path to user master key: Enter the path to the folder with user master key file. By default the master key is stored in %APPDATA%\Roaming\Microsoft\Protect\<SID>\ folder.
Please note that this folder is usually hidden, so you need to uncheck the Hide protected operating system files (Recommended) check box in the Windows Control Panel - > Folder Options -> View.
•User security descriptor: The user security descriptor is usually the name of the folder containing the user master key, and it is pre-filled by default.
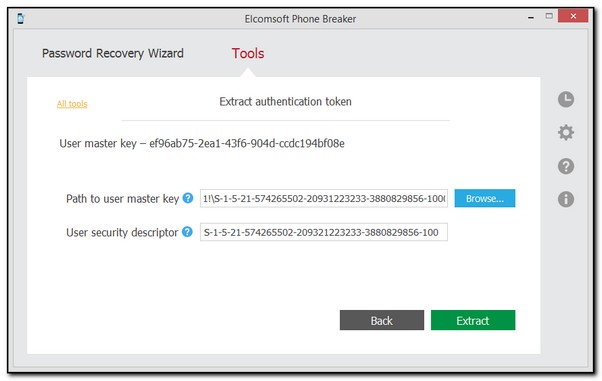
8. Click Extract.
9. The authentication token is extracted.
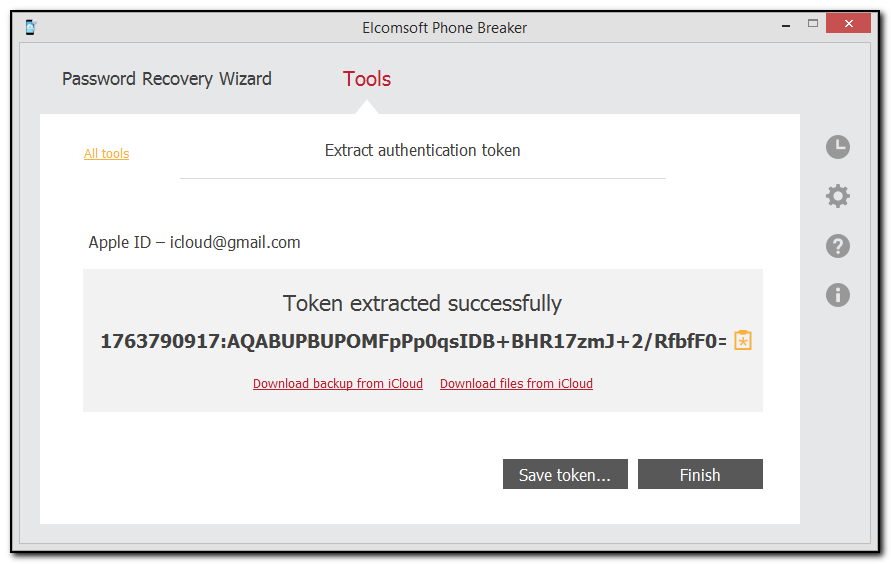
Click Save token to save the extracted string to a text file.
You can now use this token to log into iCloud and download backup from iCloud or download files from iCloud.