Choosing encryption algorithm and hash algorithm
When creating a container or image file, the user may select an optional encryption algorithm and hash algorithm. For VeraCrypt encryption, the choice of a PIM affecting .
If you know the encryption algorithm or hashing algorithm for the selected container or image file, specify this data in the window, which will greatly speed up the decryption process.
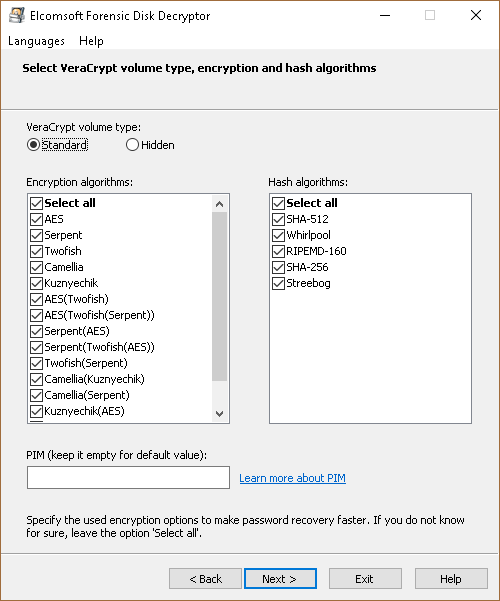
PIM
PIM (Personal Iterations Multiplier) is a value that specifies the number of iterations used by the header key derivation according to the formulas.
To encrypt the system partition that doesn't use SHA-512 or Whirlpool (faster but less secure): iterations = PIM x 2048
To encrypt a non-system partition or system encryption that uses SHA-512 or Whirlpool (slower but more secure): iterations = 15000 + (PIM x 1000)
It is not mandatory to specify a PIM. If the PIM value is left at zero, the default value will be used:
To encrypt the system partition, that uses SHA-256: iterations = 200000
To encrypt the system partition, that uses RIPEMD-160: iterations = 327661
To encrypt a non-system partition and standard containers, that uses RIPEMD-160: iterations = 655331
To encrypt a non-system partition and standard containers, that uses SHA-256, SHA-512 or Whirlpool: iterations = 500000
PIM is used in VeraCrypt since version 1.12